Last updated on April 1st, 2024 at 09:01 am
Introduction
MetaMask is a non-custodial crypto wallet that allows you to buy, spend, store, and swap crypto tokens. You can easily access the entire ecosystem of Ethereum’s Decentralized Applications (Dapps). It can further be configured to add other networks like Binance Smart Chain, Velas, Polygon etc. In January 2024, MetaMask reached 30 Million Monthly Active Users (MAUs) making it a leading non-custodial wallet across the globe.
Despite this social proof, MetaMask is a ‘hot wallet‘. There have been security concerns among its users due to the very nature of the technology it uses. One of the common ways is hackers attack Metamask wallets is by using malicious sites.
Since MetaMask is a non-custodial wallet, the wallet provider can’t be held responsible in case your wallet is hacked. If your holdings are gone, they are gone.
However, MetaMask is a very useful wallet. One of its key features is that it connects users to various decentralized exchanges (DEXs), helping them find the most profitable token swapping opportunities without any platform charges.
Just because there are a few vulnerabilities with MetaMask wallet, you, as a user, can’t just stop using it. Blockchain & cryptocurrencies are a constantly evolving space and security challenges are accordingly going to keep changing.
I would suggest if you store a huge amount of cryptocurrencies in your wallet, then you should use Hardware wallets like:
Trezor
Ledger
So, in this guide, I’ll cover the top ways hackers attack your MetaMask wallet and how you can secure it. We will be discussing attacks while it is both locked & unlocked. Let’s dive right into them.
1. Piggybacking on A Software
As I mentioned earlier, MetaMask Wallet is a “hot wallet”. So you, as a user, have to be careful about the links you click and websites you interact with. If you click on fishy links and visit dodgy sites, there are a number of ways sites or hackers can attack MetaMask wallet.
RootKit-Ed
Another common way is that you could be rootkit-ed. In case you don’t know, a rootkit is used to describe software that gains unauthorized access to your credentials and other sensitive information without you knowing.
A hacker can either get you to download unknown software or piggyback on already installed software that you use on a daily basis. Once they are successful, it is almost impossible for even the most popular antivirus software to detect this security breach.
MetaMask users have reported this as a common occurrence. For instance, a MetaMask wallet user told their story on Reddit. They suspected some kind of work causing issues with their PC. As a precautionary measure, they formatted changed hardware & RAM and even changed their router.
By the time they found out that the worm got installed on their wireless mouse’s USB, his/her MetaMask wallet got wiped clean.
Attacks like these are quite rare but they can still happen. This was just one example of how hackers attack MetaMask wallet if you click on malicious links or visit dodgy sites. This can be even worse if you are not an advanced, tech-savvy user. In many such cases, you’ll stay completely oblivious while your life savings get robbed by scammers.
2. Fake Notifications
2.1 Incoming Funds
Let’s say, you get a notification from MetaMask saying that incoming 0.1 ETH from a user has failed. What do you do?
Your first instinct would be to click on this notification to check what’s wrong. Well, don’t !! This is a common technique that scammers use in many different forms to get into your MetaMask wallet.
Let’s look at a few common ones. Outgoing Transaction Failed
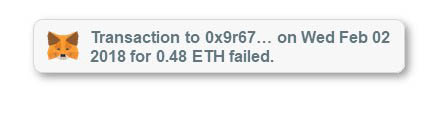
Since the crypto translations you make are on the public network, anyone can access the exact amount, the date, destination address, etc. Using this information, anyone could manifest a lookalike notification (like shown in the above screenshot).
If you click on this notification, you would be sending the same amount to a different address. And because the notification has all the data you need to believe it’s real, a normal user can easily fall for it.
2.2 Incoming Transaction
If you have been a crypto user for a while, you would know that a recipient doesn’t have to authorize an incoming transaction. There are many such small intricacies that you should know about blockchain to not fall prey to such scams.
Here’s a screenshot of a notification that is prompting a user to authorize an incoming transaction using their signature.
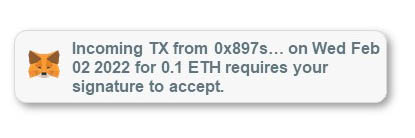
If you click on this notification and/or take the required action, you would be setting yourself to be robbed. But always keep in mind that you, as a recipient, don’t have to authorize or take any other action for an incoming transaction.
The above is a famous technique used by hackers to attack MetaMask.
2.3 Timing and Attacks
Another way hackers attack MetaMask wallets is if you visit them with an unlocked wallet. Let’s say you have an unlocked MetaMask Wallet. It could be because you are expecting some tokens or you are browsing through the Dapps.
Now here is the thing. MetaMask doesn’t exactly tell you the origin of a transaction. A malicious site could detect your unlocked wallet and present a fake transaction. Because you are expecting to make a transaction, you could be mistaken to take it as the original one.
Hackers normally use this technique on Unlocked Wallets as mentioned above which are ready to be used for transactions.
How to Safeguard your MetaMask Wallet?
These were some of the ways hackers can attack MetaMask wallets. The best way you can avoid this is:
- Don’t click on any notifications even if they look like they are from MetaMask Wallet unless you are absolutely sure that you want to give access to the site
- Always double and triple check when you are clicking on a link or opening a website on the device you’ve your MetaMask wallet.
- Don’t open any unnecessary tabs with an unlocked MetaMask wallet.
3. Lookalike Websites
This is another way hackers can attack your MetaMask wallet. You know, it is super easy to create a lookalike Metamask website for scammers and they can use it to prompt a user to take an action.
And because the details of every transaction you make in the decentralized blockchain network are accessible to everyone, anyone can recreate a lookalike MetaMask popup or website. And even the most tech-savvy users can miss intricate details to differentiate them from the real MetaMask popups & websites.
A site can copy the CSS (read, design) of a MetaMask wallet or popup it sends out. Such phony pop-ups pick up the publicly available data such as transaction history on the Blockchain network to get you to take action. The only difference between this popup and the real one would be a failed transaction.
And when you click on it to check for details, you would be making a similar transaction. Only this time, you would be making it to the scammer.
Similarly, scammers can use these fake pop-ups to get access to your login credentials. Here is a screenshot of a fake popup created by a scamming site.
Since MetaMask is a decentralized, non-custodial wallet, once someone has your login credentials (and the associated seed phrase) to your wallet they can access your tokens and make transactions.
So, how would a user know if a MetaMask site they are accessing is the right one? Here are a few things to look for.
- Always make sure that you’re downloading MetaMask wallet and extensions from the links on their original website – https://metamask.io/.
Make sure that the site you are visiting has a valid SSL certificate issued to metamask.io. Here is a screenshot of the correct format of the SSL certificate on the original website. Please note that the validity dates may change.

- Never access your MetaMask wallet or make transactions when you’re on a public network.
- Always recheck to make sure that the MetaMask Chrome/Brave extension has the namespace “nkbihfbeogaeaoehlefnkodbefgpgknn” in it. For the Firefox extension, the namespace is – ether-metamask.
Besides these, the publisher of the real Chrome extension is https://metamask.io. It comes just under the extension’s name and after the phrase “Offered by:”. These are a few identifiers, however, you may use other ways to identify the MetaMask extensions for Brave and Firefox browsers.
Final Words
MetaMask is one of the most popular non-custodial wallets out there but it is a “hot wallet“. So even though MetaMask doesn’t store your holding on their network, your wallet, in a way, is connected to the Internet. There are many ways malicious sites and scammers can fool users into making transactions or even getting their hands on your super confidential login credentials.
You, as a user, have to be extra cautious to prevent falling for these tricks. MetaMask wallet is serious about its security and even hires companies to carry out non-biased security audits for their wallet & browser extensions. Having said that, the security concerns still are real.
MetaMask, at times, recommends its users to use hardware wallets, like Ledger or Trezor, to store their funds if they have too much stake in cryptocurrencies.
As long as you are taking the necessary precautions and double-checking every transaction you make using your MetaMask wallet, you can continue enjoying its wide range of benefits. A few of them include – swapping tokens, interacting with verified decentralized exchanges, browsing Decentralized Applications or Dapps, etc.


