Last updated on March 7th, 2023 at 11:52 am
Introduction
Have you ever been browsing the web and suddenly your computer starts running really slow, or your phone’s battery drains really fast? Many people don’t realize that their computer may be infected with cryptojacking software.
It may sound scary. So let’s understand it more with answers to these questions:
- What is Cryptojacking?
- How can we detect it and Is Cryptojacking detection easy?
- How to prevent a Cryptojacking attack?
- And also the various cryptojacking software you should stay away from.
By understanding these key points, you can take steps to protect yourself and your devices from this type of attack.
What is Cryptojacking?
Cryptojacking is a type of cyber attack in which hackers use the computing power of a victim’s device to mine cryptocurrency without the victim’s knowledge or consent.
With the growth of Cryptocurrencies, it has become a growing concern for individuals and organizations alike. Cryptojacking can lead to slower device performance, higher energy consumption, and even hardware damage.
There are a number of Cryptojacking software there in the market. Cryptojacking softwares allows hackers to use your computer’s processing power to mine cryptocurrency. It’s like a virtual thief sneaking into your device and using it to make money for themselves.
And the worst part is, you may not even realize it’s happening until it’s too late.
How Cryptojacking is Carried Out?
Cryptojacking is a way in which hackers use the victim’s device to mine cryptocurrency without the victim’s knowledge or consent. According to a report by cybersecurity firm McAfee, the number of cryptojacking attack increased by 629% in the first quarter of 2018.
Another report by cybersecurity firm Symantec found that the number of cryptojacking attack increased by 8,500% in 2017. These attacks can lead to slower device performance, higher energy consumption, and even hardware damage.
It is important for individuals and organizations to be aware of cryptojacking . Take steps to protect themselves and their devices from these types of attacks. In this part, we will explore the various ways in which cryptojacking is carried out.
1. Malware Infection
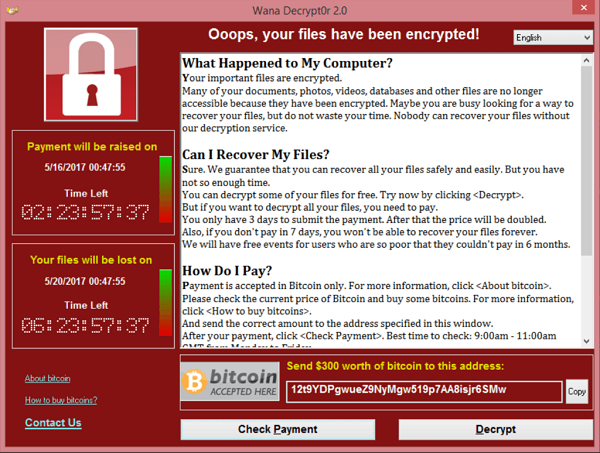
Malware infections are a common way for hackers to carry out cryptojacking attack.
Hackers use malware like trojans, viruses, and worms to infiltrate devices and mine cryptocurrency. Trojans are a type of malware that is disguised as legitimate files. They can be spread through email attachments or downloaded from the internet.
Once installed on a victim’s device, a trojan can allow hackers to remotely access the device and install cryptocurrency mining software.
The victim may not realize their device has been compromised until they notice a slowdown or faster battery drain. It is crucial to have up-to-date anti-virus and anti-malware software to protect your devices from these types of attacks.
2. Drive-By Downloads
Cryptojacking can be carried out through drive-by downloads. In this method, a victim is tricked into downloading malware by clicking on a malicious link or file.
The malware is then installed on the victim’s device and begins mining cryptocurrency in the background. One example of drive-by downloads being used for cryptojacking is through the use of phishing scams.
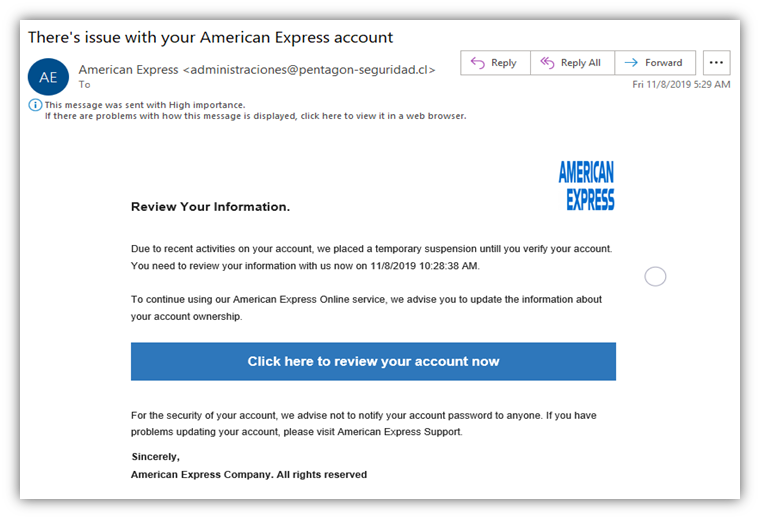
A phishing scam is when a hacker sends a victim an email. It appears to be from a legitimate source, such as a bank or online retailer. The email may contain a link or a file that the victim is tricked into clicking on or downloading.
When the victim clicks on the link or downloads the file, malware is installed on their device. It allows the hacker to mine cryptocurrency using the victim’s device. To protect against phishing scams and other types of drive-by downloads.
Users need to be cautious when clicking on links or downloading files from emails, and to only download files from trusted sources.
3. Hidden scripts on websites
Cryptojacking attacks can also be carried out through hidden scripts on websites. These scripts are inserted into a website by hackers and cause a victim’s device to mine cryptocurrency.
Some websites have been found to be using cryptojacking software to mine cryptocurrency while visitors browse their sites. It doesn’t matter how long the victim spends on the website – as soon as they visit, their device will start mining cryptocurrency for the hacker.
To prevent this type of attack, it’s essential to use an ad-blocker and only visit trustworthy websites.
For example, a victim may visit a news website that they regularly read. Unknown to the victim, the website has been compromised by a hacker. Hackers insert a hidden script for mining cryptocurrency.
As soon as the victim visits the website, their device will start mining cryptocurrency for the hacker, even in a few minutes. To protect against this type of attack, the victim should use an ad-blocker and only visit websites that they trust.
Look out for SSL certificates on the sites to make sure that they are genuine.
4. Social engineering Tactics
Cryptojacking attacks can also be carried out through social engineering tactics, where hackers use psychological manipulation to trick victims.
These tactics can include phishing scams, where victims receive fake emails that appear to be from legitimate sources (already discussed above), or phone calls or in-person interactions where victims are convinced to take actions that will compromise their devices.
To protect against scams that may result in cryptojacking, it’s important to be aware of them and to be cautious online.
For instance, a victim may receive an email that appears to be from their bank and asks them to click on a link and enter their login information. This type of attack can be prevented by staying vigilant and avoiding providing personal information in response to suspicious requests. The victim, believing the email is legitimate, clicks on the link and enters their login information.
In reality, the email was a phishing scam, and the victim has just handed over their login information to a hacker. To protect against this type of attack, the victim should be aware of phishing scams and be cautious when providing personal information or taking actions online.
Cryptojacking Detection: How to detect cryptojacking?
Cryptojacking software often uses sophisticated methods to evade detection. But Yes, there are ways to detect cryptojacking. Some common methods for detecting cryptojacking include:
1. Symptoms of cryptojacking
Decrease in Speed: First sign that a device may be compromised by cryptojacking is a noticeable decrease in performance. If you notice that your device is running slower than normal or the battery is draining faster than usual, it could be a sign that the device is being used to mine cryptocurrency.
This is because mining cryptocurrency requires a significant amount of computing power, which can strain the resources of a device and cause it to run slower.
Overheating of Device: Other symptoms of cryptojacking may include overheating of the device. If your device is getting unusually hot, it could be a sign that it is being used to mine cryptocurrency.
This is because mining cryptocurrency requires a lot of processing power, which generates heat. If your device is getting too hot, it could lead to hardware damage or shortened lifespan of the device.
Unexpected spikes in energy usage can also be a symptom of cryptojacking. If you notice that your energy bills are higher than usual or that your device is using a lot more power than normal, it could be a sign that it is being used to mine cryptocurrency. It is important to stay vigilant and protect your computer from cryptojacking software.
2. Monitoring system resources
Another way to detect cryptojacking is to monitor the system resources of a device. This can be done through the use of your systems task manager or activity monitor on a computer, or through the use of a resource monitor on a smartphone.
By monitoring the CPU, memory, and network usage of a device, it is possible to identify if there is any suspicious activity that could be caused by cryptojacking.
3. Using anti-virus and anti-malware software
Most important for cryptojacking detection is to use anti-virus and anti-malware software. These types of software are designed to detect and remove malware, including the types of malware that are commonly used for cryptojacking.
It is important to keep this software up-to-date to ensure that it is able to detect the latest threats. Security experts recommend using antivirus software and ad blockers to protect against cryptojacking software.
4. Checking for suspicious processes and network activity
Finally, it is possible to detect cryptojacking by checking for suspicious processes and network activity on a device. This can be done through the use of a network monitor or by checking the list of running processes. If there are any suspicious processes or unusual network activity, it could be a sign of cryptojacking.
By monitoring system resources, using anti-virus and anti-malware software, and checking for suspicious processes and network activity, it is possible to detect cryptojacking and take steps to prevent it from causing further damage to your device or consuming more of your resources.
How to prevent Cryptojacking?
Cryptojacking software can be used to mine various types of cryptocurrency, including Bitcoin, Ethereum, and Monero. So, In this Part, we will explore some ways to detect Cryptojacking software.
1. Malware infections
Malware infections are one of the most common ways that cryptojacking attacks are carried out. Hackers use various types of malware, such as trojans, viruses, and worms, to infiltrate a victim’s device and install software that allows them to mine cryptocurrency. This can be done through email attachments, malicious websites, or even legitimate websites that have been compromised.
To protect against malware infections, it is important to have up-to-date anti-virus and anti-malware software installed on your devices.
These types of software are designed to detect and remove malware, including the types of malware that are commonly used for cryptojacking. It is important to keep this software up-to-date to ensure that it is able to detect the latest threats.
In addition to using anti-virus and anti-malware software, it is also important to be cautious when clicking on links or downloading files from the internet.
Hackers often use these methods to spread malware, so it is important to be careful and only download files from trusted sources. It is also a good idea to avoid clicking on links in emails or messages from unfamiliar sources, as these could potentially be malicious.
2. Ensuring website security
Hackers can insert code into a website that will cause a victim’s device to mine cryptocurrency when the website is visited. This type of attack, known as “cryptojacking through hidden scripts,” can happen even if the victim is only visiting the website for a short period of time. To protect against this type of attack, it is important to ensure website security.
One way to ensure website security is to use an ad-blocker. Ad-blockers can prevent advertisements from being displayed on websites, which helps prevent hidden scripts from being executed on a victim’s device.
It is important to note that not all ad-blockers effectively block cryptojacking scripts. So it is a good idea to research and choose an ad-blocker specifically designed for this purpose.
In addition to using an ad-blocker, it is also important to only visit websites that you trust. Hackers can insert hidden scripts into any type of website, including legitimate websites that have been compromised.
By only visiting websites that you trust, you can reduce the risk of falling victim to a cryptojacking attack through hidden scripts.
Ensuring website security is an important part of protecting against cryptojacking. By using an ad-blocker , you can reduce the risk of your device being compromised by a cryptojacking.
Real Life Example of Cryptojacking
- In 2019, Microsoft Store removed eight apps that secretly mined cryptocurrency using the resources of those who downloaded them. It was believed that a single individual or organization created these apps. It was released under the names of three different developers.
Potential victims could easily find these cryptojacking apps through keyword searches or lists of popular free apps in the Microsoft Store. - Cryptojacking code was found on the Los Angeles Times’ Homicide Report page in 2018. When people visited this page, their devices were used to mine Monero, a popular cryptocurrency, without their knowledge.
The threat went undetected for a while because the script only used a small amount of computing power. So many users were unaware that their devices had been compromised. - In 2018, a European water utility control system’s operational technology network was targeted by cryptojackers, severely affecting the operators’ ability to manage the plant. This was the first known instance of a crypto-jacking software attack on an industrial control system. Like the attack on the Los Angeles Times, the miner in this case was generating Monero.
Conclusion
To protect against cryptojacking attacks, it is important to keep your operating system and antivirus software up to date and use only trusted sites.
Users need to be cautious when opening email attachments or downloading files. You can also use browser extensions that block cryptocurrency mining scripts to protect your computer from drive-by mining attacks.


